In rule-based systems, which takes precedence: a deny rule or a allow rule?
Published 10 months ago
# SafeLine WAF
Published 10 months ago
gun young
Updated 8 months ago
3
Answer: The allow rule has the highest priority among all rules.
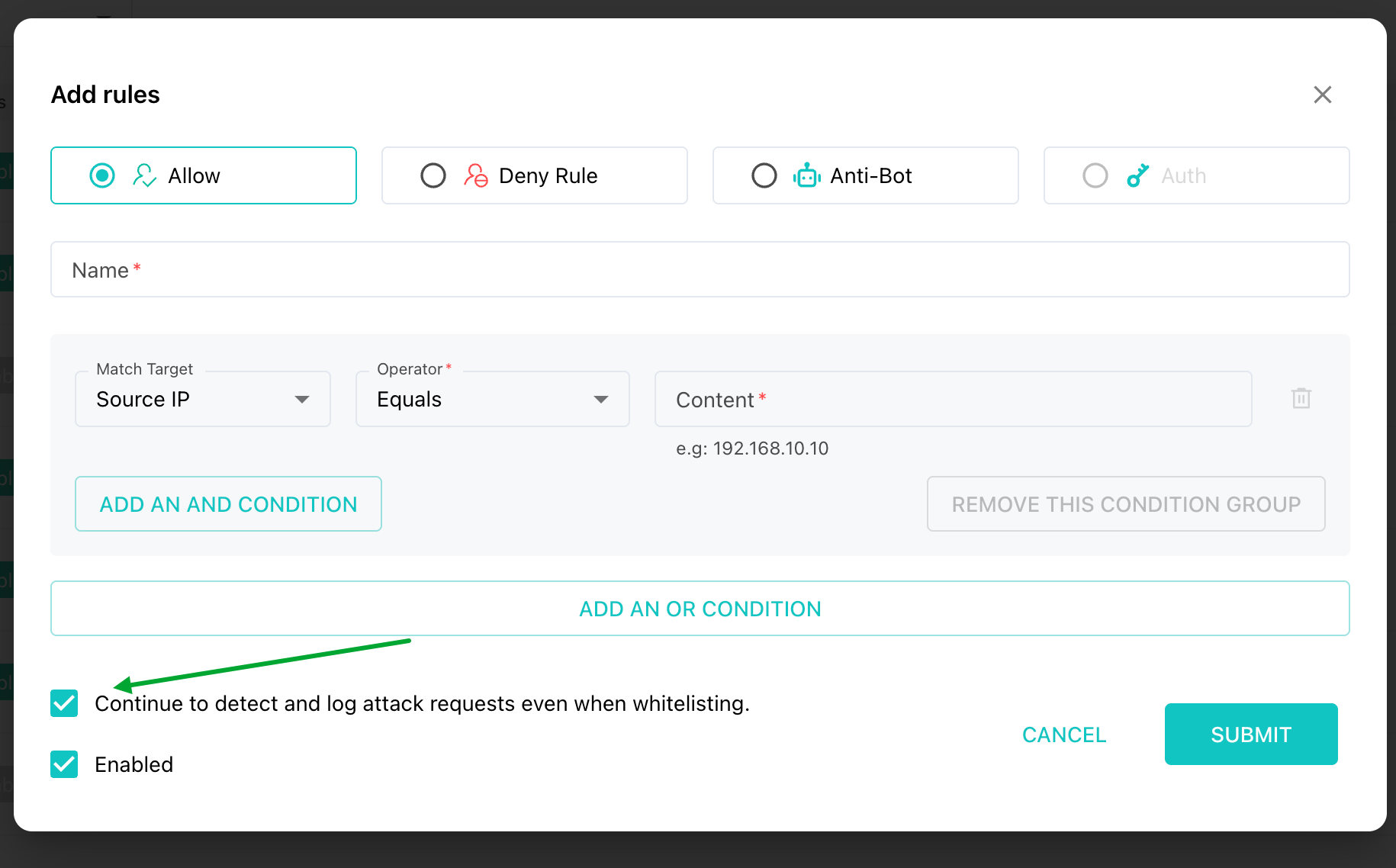
If a request matches a allow rule, it will bypass all other security checks—even if it is flagged as malicious by the WAF—and proceed directly to your server.
Therefore, when configuring allow rules, we strongly recommend:
Use allow rule with extreme caution.
Enable the "Continue to detect and log attack requests even when whitelisting." option.
This ensures that if attackers exploit your allow rule to infiltrate your website, you can immediately review attack details in Attack > Logs and take remedial action.
Nghĩa Nguyễn
Updated 7 months ago
0
Ok
Mahufooz MAHOO SAAND
Updated 7 months ago
0
Mohamed Mahfooz
Ok
Mahufooz MAHOO SAAND
Updated 7 months ago
0
Mohamed Mahfooz
Ok